William A. Radasky
IEEE Life Fellow
WHAT IS IEMI?
In recent years, Hollywood has indicated that criminals and terrorists could use electromagnetic (EM) weapons to black out a portion of Las Vegas (Ocean’s 11) or take down a counter-terrorism computer center (24). Is this fact or fiction? It turns out that Hollywood in this case is leading the public and police agencies in understanding the possibilities of this threat. As with fiction, however, these two examples are extreme in the sense that they either used a large generator to connect to the wiring of a power substation or an explosive device in the trunk of an automobile. Neither of these situations are the most likely ways that EM weapons would be used against the critical infrastructures.
In the late 1990s, two respected International scientific and engineering organizations took initial steps to understand the threat of electromagnetic weapons on society. In 1999, URSI (International Union of Radio Science) passed a resolution at their General Assembly Meeting in Ottawa, Canada recommending that scientists and engineers take this threat seriously and work to protect against it. In the same year, IEC SC 77C expanded their scope of work to begin to write reports and standards dealing with what was originally called EM Terrorism, but was later renamed as Intentional Electromagnetic Interference (IEMI). IEMI has been formally defined as: “Intentional malicious generation of electromagnetic energy introducing noise or signals into electric and electronic systems, thus disrupting, confusing or damaging these systems for terrorist or criminal purposes.”
The reason that this threat has emerged in recent years is two-fold. First, powerful solid-state electronics allow the development of electromagnetic weapons that produce high levels of peak power in very short time domain pulses; as the objective of these weapons is to produce high peak electric and magnetic fields, the energy contained in the pulses is not as important. This allows the use of a small energy source to power the weapons. Second, modern commercial electronics and computers operate with microprocessors with clock speeds in the GHz range and at low internal operating voltages, making them potentially more susceptible to interference and damage to EM threats in this same frequency and voltage range.
A few cases of IEMI threats/attacks have been well documented, but many more are not discussed in public due to the embarrassment of those attacked or for security reasons. Here are a few illustrative examples.
- In Japan, two Yakuza criminals were caught using an EM weapon on a Pachinko (gaming) machine to trigger a false win.
- In St. Petersburg, Russia, a criminal used an EM weapon to disable a security system at a jewelry store, so that he could commit a robbery.
- In London a city bank was the target of blackmail attempt whereby the use of an EM weapon was threatened against the bank’s systems.
- In Moscow a Telecommunications center was targeted and was put out of commission for 24 hours, denying service to 200,000 customers.
- In early March 2011, the city of Seoul, Korea sustained an electronic jamming attack that disabled a large number of GPS systems used in industry. In addition the South Korean military indicated that some of their systems had been adversely affected. In early 2012, it was also reported that GPS systems in the region of the Incheon International Airport in South Korea were being jammed and that airlines were warned about this situation.
INTRODUCTION
Electromagnetic weapons consist of two categories: radiated and conducted. Both types possess an energy source (such as a battery), a solid state generator that produces high output voltages with a rapid variation in time, and either an antenna that is designed to propagate these fields some distance away from the weapon (radiated fields) or a means to connect to wiring of a system (conducted voltages). The radiated fields are more flexible (for the attacker) but they decrease rapidly with distance from the weapon. The conducted weapons require a connection to power or data lines outside of a building, but their entire output is transmitted to the circuits they are attacking. One might think that the conducted threat is not important, however, buildings have been found to have unprotected data cabinets and external power plugs outside of the building. In addition, attackers with power system experience can connect to the low voltage outputs of transformers leading into buildings.
Figure 1 illustrates the basic process for “coupling” radiated fields from an EM weapon into a building. The electromagnetic fields will induce voltages and currents on both external and internal wiring (for the internal wiring the shielding properties of the building are important). These voltages will lead to electronic equipment that often cannot tolerate the levels entering the equipment. Providing line protection (surge arresters/filers) at the entrance of external building cables and providing some electromagnetic shielding in the building walls will provide some protection against this threat (discussed later).
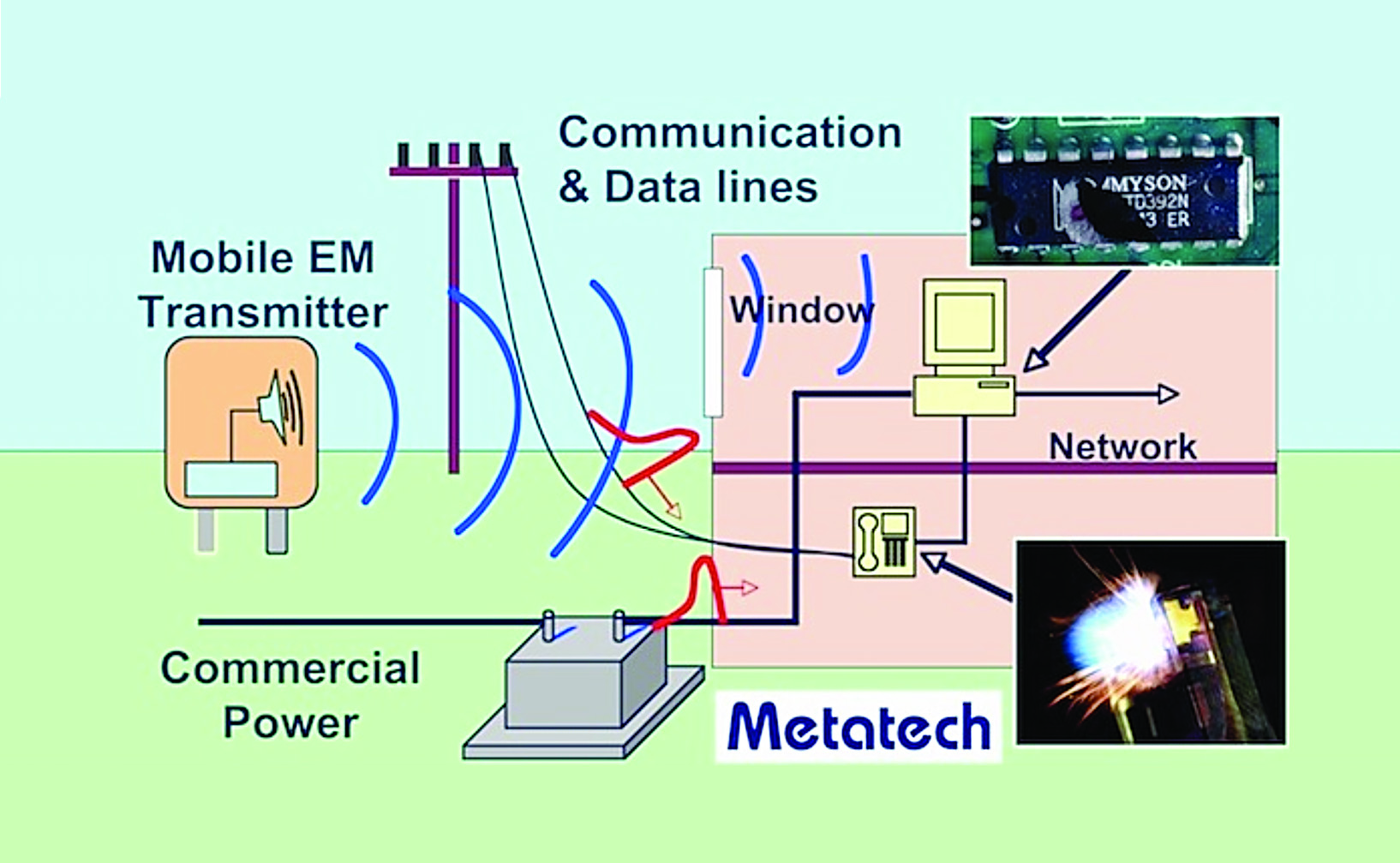
As for the critical infrastructures such as the power, telecommunications, financial, water, natural gas, etc., nearly all of these infrastructures are controlled by computers with more and more sophistication each year. For example the power systems in developed areas of the world are installing digital smart power meters at homes and businesses along with communications systems to transmit the data. In addition, distributed renewal power systems require additional sensors to determine their operating status so the grid can operate efficiently. The increase in the amount of information to be processed and the accompanying communications requirements make the system more vulnerable to those who wish to create problems (whether they be hackers, criminals or terrorists).
While security is always an important consideration for the critical infrastructures, it must be noted that locked doors or even fences are not an impediment to EM weapons. In addition an attacker can try to disrupt a facility over and over until they succeed, as no one will know that they are under attack until computer problems are noticed.
TECHNICAL BACKGROUND
EM Weapon Characteristics
In order to understand the threats to electronic equipment, it is necessary to understand the different types of electromagnetic environments that can be produced and that can create operational problems for exposed equipment. There are two basic categories of EM environments of concern: narrowband and wideband. Also as mentioned earlier, there are also two major ways for this power to be delivered to a system: through a radiated or conducted process.
A narrowband waveform is nearly a single frequency (typically a bandwidth of less than 1% of the center frequency) of power delivered over a fixed time frame (from 100 nanoseconds to microseconds). Some of the environments in this category include modulation of sine waves, shifting frequencies and even repetitive applications. This category of threat is usually referred to as high power microwaves (HPM), although this term is used loosely to include frequencies outside of the microwave range.
A wideband waveform (sometimes referred to as ultrawideband – UWB or short pulse – SP) is usually one in which a time domain pulse is delivered, often in a repetitive fashion. The term “wideband” usually indicates that the power in the waveform is produced over a substantial frequency range relative to the “center frequency”. Of course many pulse waveforms do not have an explicit center frequency and the technical community decided that there was a need for better definitions relating to this problem. The IEC has defined new terms to describe wideband waveforms including mesoband, subhyperband and hyperband [IEC 61000-2-13].
In terms of system vulnerabilities, the narrowband threat is usually one of very high power, since the electrical energy is delivered in a narrow frequency band. It is fairly easy to deliver fields on the order of thousands of volts/meter at a single frequency. Often the malfunctions observed in testing equipment with narrowband waveforms are those of permanent damage.
The wideband threat is somewhat different in this respect. Since a time domain pulse produces power over many frequencies at the same time, the power produced at any single frequency is much less. This means that damage is not as likely as in the narrowband case. Sources that have been built can produce repetitive pulses up to 1 million per second and can continue for many seconds or minutes, thereby increasing the probability of producing a system upset. Some of these upsets can interfere with the communications of data, thus providing a different type of denial of service.
One example of an extremely powerful wideband generator was developed by the U.S. Air Force for research purposes. It is known as the JOLT simulator and its capabilities were published in the IEEE Proceedings in July 2004. A photograph of the generator is shown in Figure 2.

Vulnerability of Commercial Electronics
Over the past fifteen years there have been significant experiments that have tested the response of commercial equipment to narrowband and wideband threats similar to those expected from IEMI. In general this testing has emphasized personal computer equipment (including networks) since they are in wide usage in many different industries. In addition testing has included cash machines, industrial control equipment, power supplies, Ethernet components, WIFI networks, automobiles, GPS electronics, cellular phones, PDAs and different types of sensors. Many journal articles and conference papers have dealt with the details of these experiments, and therefore we will only summarize the results here.
Modern computers and other types of equipment using microprocessors appear to be vulnerable to malfunction from radiated narrowband fields above 30 V/m, although newer high-speed PCs have higher susceptibility levels (~300 V/m). There appear to be large variations in the responses of equipment due to the specific experiment setups and the quality of the equipment enclosures that are used. In addition, tests performed over the range of 1 – 10 GHz seem to indicate that malfunctions occur at lower field levels at lower frequencies.

Wideband radiated-field testing has also been performed by Russian, Swedish, German and U.S. scientists. Testing of computer-sized electronic equipment indicates that peak electric field levels of ~2 kV/m for pulses with pulse widths on the order of 200 ps create upset in the electronics (requiring a power reset), with damage occurring in the 5 kV/m range. An example of circuit board damage caused by a pulsed voltage that represents coupling to a metallic Ethernet cable is shown in Figure 3.
One should note that these experiments are usually performed by directly exposing the equipment under test within line of sight of a radiating antenna. Of course if the equipment is inside a building or in a room without a window, there will be a reduction of the incident field from outside to inside (depending on the type of wall construction). Also most experiments have not carefully examined the polarization and angle of incidence aspect thoroughly (due to time and expense aspects), and therefore most of the effects noted during testing can occur at even lower field levels when an optimum coupling geometry is considered.
For conducted IEMI threats, it seems clear that if attacker access to external telecom or power cables is not prevented, it is fairly easy to inject harmful signals into a building. For pulsed waveforms, it appears that pulse widths on the order of 100 microseconds can create damage to equipment power supplies and to interface circuit boards at levels as low as 500 volts, but more typically at levels of 2 – 4 kV.
Relationship to IEC EMC Immunity Standards
While these failure values may seem to be low with respect to the capabilities of EM weapons, they should not be a surprise. When one examines the everyday electromagnetic compatibility (EMC) test requirements for immunity in the IEC, it is unusual to see a narrowband radiated field level immunity requirement above 10 V/m (for frequencies above 80 MHz). Higher levels are not recommended for home or factory applications because of the expense of providing the increased protection.
For wideband-conducted transients, most of the lightning and electric fast transient tests for EMC are performed for levels up to 2 kV. Only in special cases, such as for equipment in a power generating facility or a substation, will the immunity test levels be higher. The typical EMC conducted wideband test waveforms (such as the EFT) have rise-times as fast as 5 ns and pulse widths as long as 700 microseconds (e.g. 61000-4-5). The narrowest pulse width for EMC is 50 ns, which is much wider than the typical IEMI threat.
It is therefore clear that the EMC immunity levels of commercial electronics are low compared to their apparent susceptibility levels to IEMI electromagnetic environments. This indicates that normal EMC immunity protection will not be sufficient for the IEMI problem. In addition, when a generator like JOLT is used, it can produce 50 kV/m at a range of 100 meters distance. This exceeds the damage level for most unprotected electronics by a factor of 10!
Protection Approach
The basic IEMI protection approach for a building housing sensitive electronics consists of ensuring that all cables entering a building from the outside are protected at their entrance with filters and surge protection devices with a good low inductance grounding system. This is necessary since the frequency content of the coupled disturbances will be above 100 MHz and a simple ground wire will have a high impedance. The second approach is to reduce the external fields penetrating the building. For the fields that do penetrate, there are options available to deal with the residual internal electromagnetic fields.
Several options for mitigation include:
- Better electromagnetic building shielding. Increase the quality of the shielding effectiveness of the building in the frequency range of importance. For example, windows are leaky to high frequency EM fields, and should be covered over with metal sheeting or a metallic screen.
- Increase the possible weapon standoff distances using physical security, such as fencing, to keep assailants far away, in order to take advantage of the 1/R falloff in electric field from an antenna.
- Use EM alarms to monitor the EM environment – watch for the start and continuation of an IEMI attack.
- If high levels of IEMI fields can get into the facility and couple to network cabling, then an effort must be made to either reduce the coupling to the cables or restrict the effects of the coupled signals. Approaches to accomplish this include:
- Lay out cables along metallic surfaces.
- Use shielded cables and connectors.
- Use ferrites on metallic cables.
- Use surge protection devices at the equipment connection.
- Use optical cabling without metal to replace metallic cable.
Building Shielding
Depending on the strength of an IEMI weapon and its location relative to the electronics, it is conceivable that the external peak electromagnetic fields will be greater than 10 kV/m. These fields may not be attenuated very much in the range of 1 MHz to 5 GHz, depending on the natural shielding provided by typical construction methods. Table 1 shows the results of measurements at buildings with different types of construction materials. It is clear that there is a strong variation in attenuation. The far right column indicates the measurement values obtained, while the first column places the measurements into approximate categories.
There are two approaches in dealing with the building itself. First one could improve the shielding effectiveness by covering open windows, if present, covering the external surfaces of the building with metallic material, adding metallic materials to the internal walls of the building (metallic wallboard), or replacing the existing building with an all metal building (clearly the most expensive option). In addition, irrespective of the approach taken, any external power, communications and control cables must be grounded at the building entrance with low inductance techniques (plates not wires).
Electromagnetic Alarms
Since in many cases EM weapons may create major interference with computers and other electronics only while the weapon is transmitting, there is some value in using a detector to determine if a continuous IEMI source is operating nearby. Even if the attack were short in duration, a detector would be useful from a forensic point of view. Because of the wide range of EM environments (from narrowband to hyperband), it is not easy to build detectors that can cover a large range of frequencies and time intervals, but Figure 4 shows one example of a portable detector (it can detect frequencies up to 8 GHz). Other detectors can be installed permanently near sensitive electronics.

Protection Activities
As indicated in the introduction of this article, after the URSI resolution, the IEC started its standardization work dealing with IEMI in earnest. This then led to activities within the IEEE, ITU-T and Cigré as indicated below:
- IEC IEMI standards development began in 1999.
- The IEEE EMC Society Transactions Special Issue on IEMI was published in August 2004.
- The ITU-T Recommendation for the protection of telecommunications systems from HPEM (IEMI), K.81 was published in 2009.
- The IEEE EMC Society Standard Practice P1642 under development to protect publicly accessible computers from the threat of IEMI is planned for publication in 2014.
- A Cigré C4 Brochure is under development for the protection of high-voltage power substation control electronics from IEMI and is planned for publication by the end of 2014.
In addition to standardization activities, the Federal Energy Regulatory Commission and the U.S Department of Energy have evaluated the impact of severe electromagnetic threats on the power industry, and the U.S. House of Representatives has introduced the SHIELD Act, HR 668, which if passed into law will require the protection of the bulk power electric infrastructure against the threats of natural and man-made electromagnetic pulse. IEMI is one of these man-made threats.
CONCLUSION
While electromagnetic weapons may seem to be something conjured up by Hollywood for entertainment, they are clearly threats to modern electronic systems due to advances in both solid state electronics for producing small advanced weapons and also due to the increased efficiency of electronics operating at lower and lower voltages (increasing their sensitivity).
From the brief overview presented here, it is clear that the international technical community has evaluated the situation and feels that IEMI is a real threat to our critical infrastructures. Through research and engineering studies, several ways have been revealed to make our society less vulnerable to this threat. The challenge for the future is to determine the most cost-effective approaches for protection that include physical protection, electromagnetic protection and finally electromagnetic detection. In addition the education of facility operators is an important goal, which hopefully is promoted by this article.
For Further Reading
Standards produced by IEC SC 77C dealing with HPEM and IEMI (www.iec.ch)
“Special Issue on High-Power Electromagnetics (HPEM) and Intentional Electromagnetic Interference (IEMI)”, IEEE Transactions on Electromagnetic Compatibility, Volume 46, No. 3, August 2004.
“High-power electromagnetic immunity guide for telecommunication systems,” Telecommunication Standardization Sector of ITU, ITU-T, K.81, November 2009.
William Radasky received his Ph.D. in Electrical Engineering from the University of California at Santa Barbara in 1981. He has worked on high power electromagnetics applications for more than 46 years. He has published over 450 reports, papers and articles dealing with electromagnetic environments, effects and protection during his career. In recent years he has worked extensively in performing assessments for critical infrastructures to the threats of HEMP, IEMI and severe geomagnetic storms. He is Chairman of IEC SC 77C (EMC: High Power Transient Phenomena), Chairman of IEEE EMC Society TC-5 (High Power EM), and a Working Group Convener for Cigré C4. He founded Metatech Corporation in 1984 in California and is the president and managing engineer.
Radasky is very active in the field of electromagnetic compatibility (EMC) standardization, and he received the Lord Kelvin Award from the IEC in 2004 for outstanding contributions to international standardization. He is an IEEE Life Fellow and a registered professional engineer in electric engineering.
