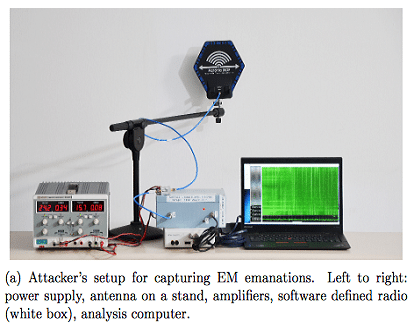
In recent years, “air-gapped” computers, which are disconnected from the internet so hackers can not remotely access their contents, have become a regular target for security researchers. Now, researchers from Tel Aviv University and Technion have gone a step further than past efforts, and found a way to steal data from air-gapped machines while their equipment is in another room.
“By measuring the target’s electromagnetic emanations, the attack extracts the secret decryption key within seconds, from a target located in an adjacent room across a wall,” Daniel Genkin, Lev Pachmanov, Itamar Pipman, and Eran Tromer write in a recently published paper. The research will be presented at the upcoming RSA Conference on March 3.
“The attack in its current form uses lab equipment that costs about $3000 and, as shown in the photos, is somewhat unwieldy,” Tromer reports. “However, experience shows that once the physical phenomena are understood in the lab, the attack setup can be miniaturized and simplified.”
“The attacks are completely non-intrusive, we did not modify the targets or open their chassis.” The method is a so-called side-channel attack: an attack that doesn’t tackle an encryption implementation head on, such as through brute force or by exploiting a weakness in the underlying algorithm, but through some other means. In this case, the attack relies on the electromagnetic outputs of the laptop that are emitted during the decryption process, which can then be used to work out the target’s key.
Specifically, the researchers obtained the private key from a laptop running GnuPG, a popular implementation of OpenPGP. (The developers of GnuPG have since released countermeasures to the method. Tromer said that the changes make GnuPG “more resistant to side-channel attack since the sequence of high-level arithmetic operations does not depend on the secret key.”)
“During the decryption of the chosen ciphertext, we measure the EM leakage of the target laptop, focusing on a narrow frequency band,” the paper reads. The signal is then processed, and “a clean trace is produced which reveals information about the operands used in the elliptic curve cryptography,” it continues, which in turn “is used in order to reveal the secret key.”
The equipment used included an antenna, amplifiers, a software-defined radio, and a laptop. This process was being carried out through a 15cm thick wall, reinforced with metal studs, according to the paper.
For more, click here. To read the paper, click here.
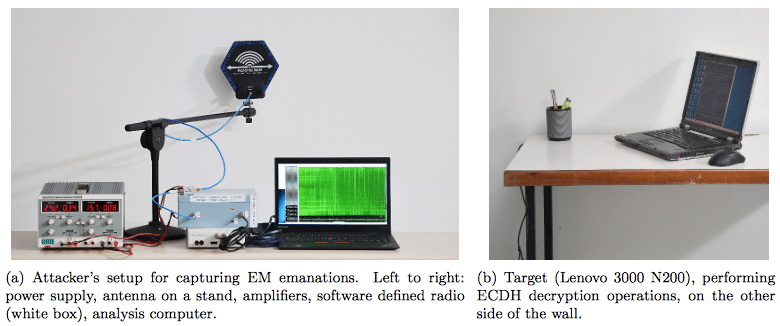 Image courtesy of Technion and Tel Aviv University.
Image courtesy of Technion and Tel Aviv University.